Getting A Ransom Email From An Alleged Hacker
You’ve probably heard about those emails that have been going around for a few years now where a website owner gets an email demanding that a ransom be paid or their site will be damaged, their reputations damaged and/or database content being released or sold for profit.
Well, I got one of those emails yesterday – it’s actually the first one I’ve ever received.
The ransom email was for one of my other websites hosted with a different web hosting company (GreenGeeks) than the site you’re currently on is.
Anyway, here’s the email (I’ve blurred out some info for privacy/security reasons)…
 Click the image for a full-sized view
Click the image for a full-sized view
Could This Email Be From A Real Black Hat Hacker?
Is it possible that a hacker did find a vulnerability to exploit on my site?
Absolutely, yes, despite the security plugins I use (and keep up to date) and running the site through Cloudflare for extra security.
Colorlib estimates that there are around 810 million WordPress sites as of 2023.
This represents around 43% of all websites, and that figure is growing rapidly.
In fact, over 500 sites are built with WordPress every day.
Colorlib also estimates that about 13,000 WordPress sites are hacked each day.
To be honest, these figures seem on the low side to me.
A few years ago, it was estimated (by other sources) that 30,000 sites were hacked daily.
WordPress Security
According to another source – CreativeMinds – there are 90,000 hack attacks (not necessarily successful), not per day, but per minute, on WordPress sites globally.
Whatever the actual figures are, it’s clear that there are more than enough WordPress sites to make them a popular target for hackers.
Security measures and hackers are in a constant arms race as one tries to break through or stop the other.
It’s why you need to use security plugins in the first place on WordPress sites and why you need to keep them up to date to counter any vulnerabilities that may have been found.
A lot of hacks attempts are successful because webmasters are lax when it comes to WordPress security and site maintenance.
Plugins and themes don’t get updated for weeks or even months and/or weak login credentials are used which make it easy for a hacker to access the backend of a site.
When I first started using WordPress back in the early 2010s, my sites were frequently hacked.
I knew nothing about hardening a WordPress site against hackers or that I even needed to use security plugins, which were not as readily available back then as they are today.
Days and even weeks wasted repairing and rebuilding sites educated me pretty quickly on how important site security actually is and now all my sites are protected by a variety of plugins and other security measures.
You can and should run a regular site security check on any WordPress blog you own just in case that site has been successfully hacked.
Your site may look like it’s fine on the surface but it could be infecting visitors with malware all the same.
Site Security Measures Outside of WordPress
Some web hosts provide a cPanel app like Imunify360 that you can run to check for malware.
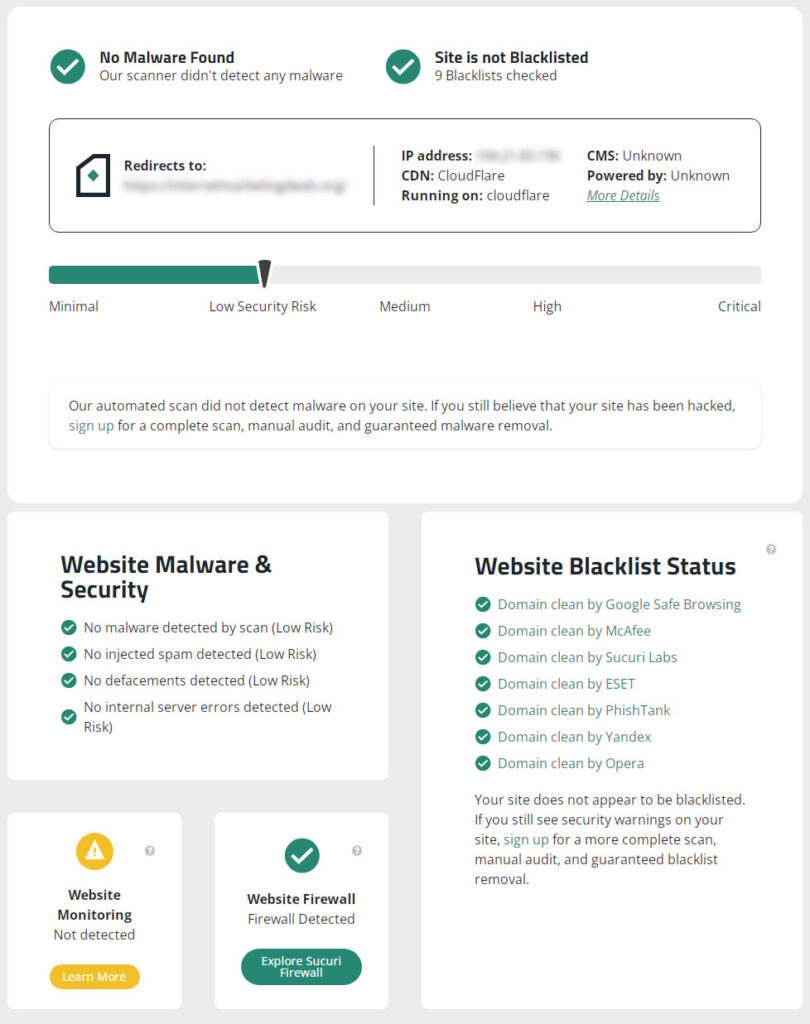
You can also run your site through the Sucuri Site Checker to get a free malware and site security check.
Here are the results for my site which the hacker claims he’s gained access to:
Some web hosts apply their own security measures, in addition to anything I might add to my sites, so there are two, possibly three levels of site security in play for any given site.
A Closer Look At The Hacker’s Email
The above email looked very generic to me with my site’s name being dropped into it to make it unique.
For one thing, there’s only one user in my site’s database – me.
There are no clients/customers/subscribers whose information can be leaked or sold, so the email referring to “customers/associates” is not applicable.
For that reason, I believe that this email is nothing more than a fishing expedition looking for a gullible webmaster to panic and pay the ransom fee.
Kirk Tarenorerer (the email sender) is likely a fake name and I could not find anything in Google related to him.
There is a Kirk Tarenorerer account on Facebook, but there is absolutely nothing in that account and it may belong to a legitimate person of that name.
I did a bit of research on the hacker@peluconburgos.es email address and domain.
peluconburgos.es is a real domain based in Spain and appears to be hair salon site.
I pinged the hacker@peluconburgos.es email address and got back this error:
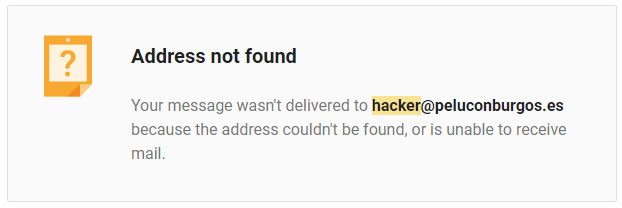
So that could mean that the peluconburgos.es site has been hacked itself and the hacker has hijacked their email account to create a temporary email address to use to send the email to me.
And then deleted that email address.
Another possibility is that someone associated with peluconburgos.es is actually creating temporary email addresses just to send out these kinds of email.
What About The Hacker’s Bitcoin Address?
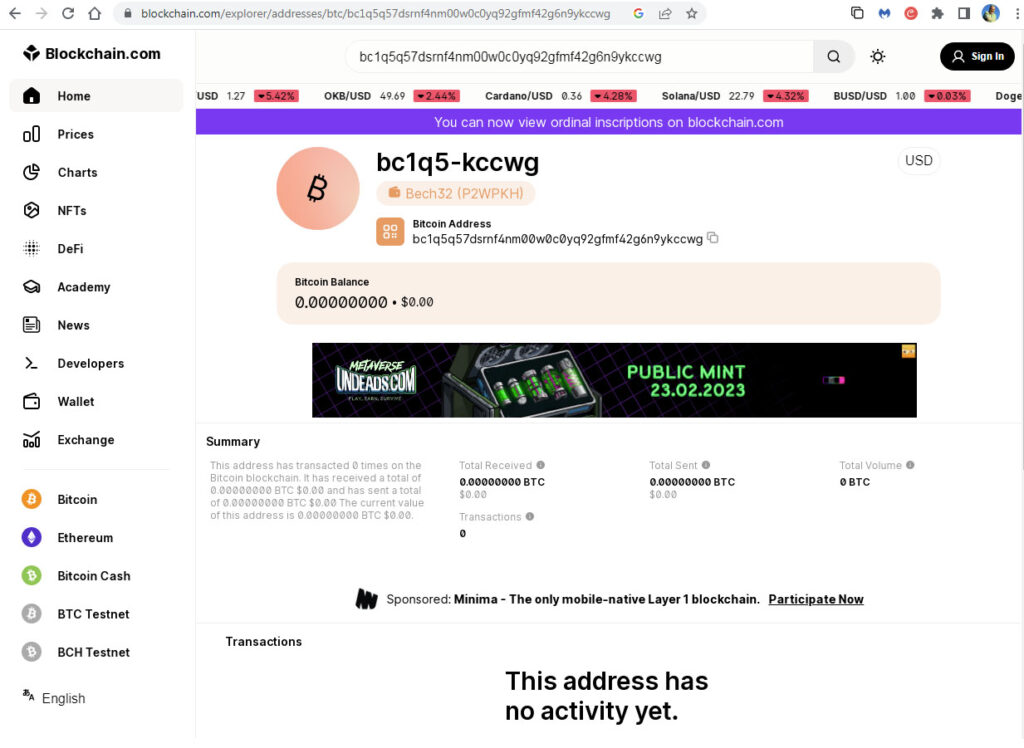
So next I checked the Bitcoin address to see if there have been any transactions on it.
You can check the transactions for any Bitcoin address/wallet by going to the BlockChain Explorer and pasting in the Bitcoin address of interest.
This won’t tell you who the owner of the address/wallet is, but you can track how funds move across the cryptocurrency exchanges.
Here are the results for the hacker’s Bitcoin address:
 Click the image for a full-sized view
Click the image for a full-sized view
So no transactions to date on this Bitcoin address.
Now, it’s possible that this address was created specifically for me to use so that the hacker would know I’d made their requested payment.
Or it could be a catchall Bitcoin address where the hacker has been completely unsuccessful in extorting money from other webmasters.
Learning More About The IP Address At The Bottom of The Email
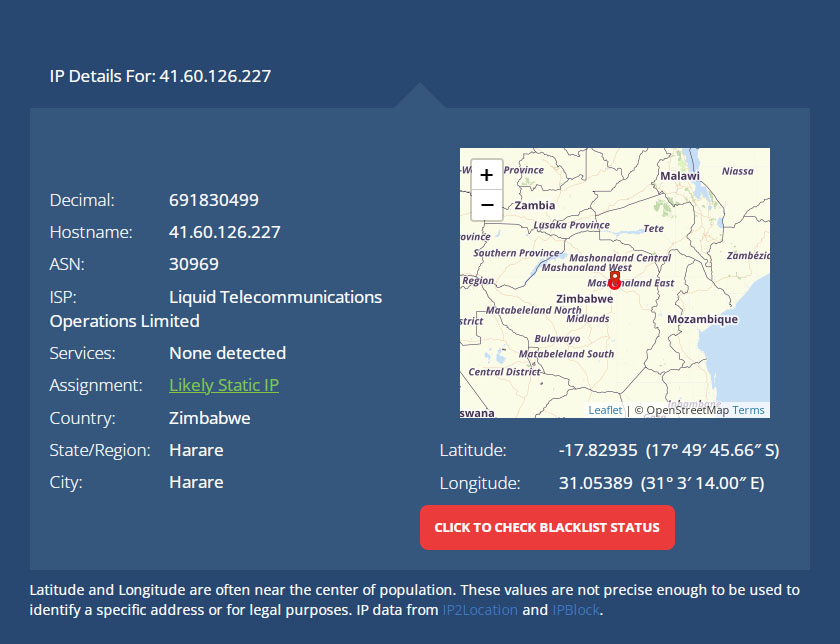
See that IP address at the bottom of the above email?
I put that into an IP address Lookup site to see where it’s actually located.
You can check it for yourself at: https://whatismyipaddress.com/ip/41.60.126.227
And here are the results:
Now, if you click the Click To Check Blacklist Status button on the above page, you’ll get taken to a list of sites where the IP address is either flagged as okay or blacklisted.
Most sites list the IP address as ok, but two didn’t – The Spamcop Blacklist (online since 1992 and checking for IP addresses used for spam) and UCE Protect which maintains a DNS blacklisting service.
So this IP address is known to some blacklist directories.
I don’t know if I should read anything into the fact that the IP address is in Zimbabwe (Africa).
Feedback From My Web Host
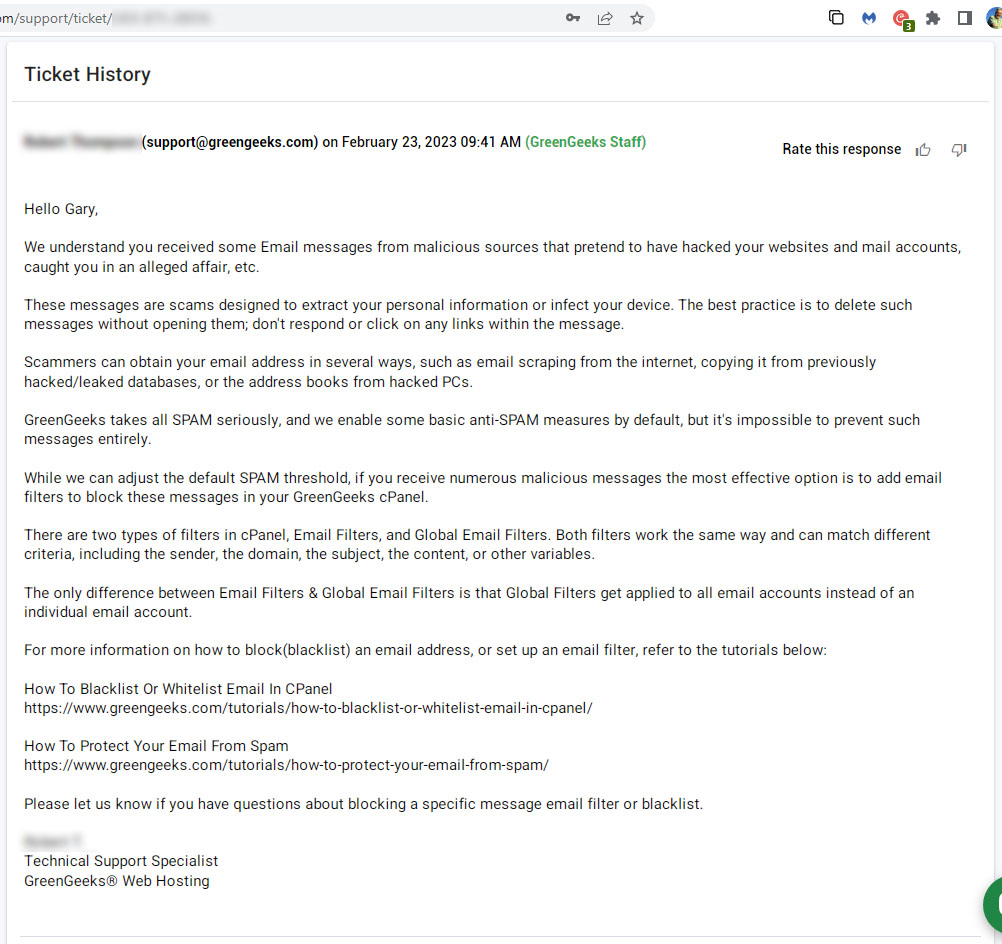
I emailed a copy of the hacker’s email to my web host to alert them about a potential hack attack in a couple of days.
This was their reply:
So GreenGeeks think this is just a scam email…just as I do.
At least now they’re alerted on the small chance that this is a real threat.
My site isn’t worth anywhere close to the $3,500 being demanded in ransom so, no, I won’t be paying the extortioner.
And, if my site is hacked or defaced, etc.?
Well, I have a full site and database backup (created days before I received the ransom email) that I can use to rebuild the site in a few minutes.
Besides that, GreenGeeks will have their own backup of my site that they can restore if I ask them to.
Final Thoughts
If you run WordPress blogs, then you need to be constantly vigilant where site security is concerned.
Just because you receive a ransom email like the one above doesn’t automatically mean that your site has been hacked.
On the other hand, if you never receive a ransom email, that doesn’t mean that your site has not been hacked.
Extorting ransoms from web site owners isn’t the only reason to hack a site.
If your site holds sensitive data, then that can be sold on the black market without your knowledge, opening up customers, clients, subscribers, etc. to email phishing attacks, being sent spam emails and so on.
It might be to replace your affiliate links with theirs, for example, so they make money off your site instead of you.
Or it might be to spread malware to the devices that people use to view your site.
I take care of my sites and make sure they’re kept up to date – I don’t want a repeat of what happened to me when I first started using WordPress and was clueless about site security.
There’s no guarantee that the WordPress security plugins you use will stop all hack attacks because things change very fast in this arena.
So make sure you look after and maintain your own sites and regularly run a site security check.

All the best,
Gary Nugent
Check out my Instagram posts and reels here:
Follow me (@garynugentmentoring) on Instagram
P.S.: Don't forget, if you want to create an internet income of your own, here's one of my recommended ways to do that: